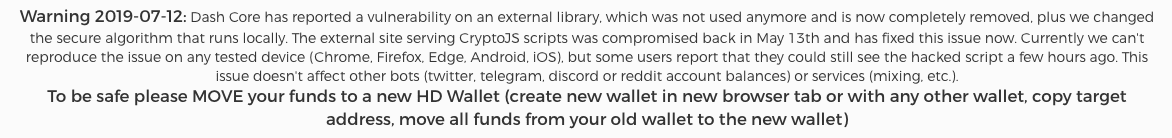
“The hacker was able to obtain private keys used between May 13 and July 12,” wrote Dash marketing manager Michael Seitz in a July 12 Dash forum post. Inspired by MyEtherWallet, MyDashWallet acts as an online wallet for fledgling altcoin DASH. The service, which runs almost entirely on JavaScript, allows users to store, send, and receive DASH from within their web browser. “Out of an abundance of caution, anyone using mydashwallet.org in that timeframe should assume their private keys are known by the hacker and should immediately move any balances out of that wallet,” he added.
Insecure coding practices went undetected for over a year
A separate Dash representative explained that changes had been made to MyDashWallet in April 2018 that saw it begin to load an external script from third-party host GreasyFork. Hackers are said to have gained access to the GreasyFork account of that script’s creator to add malicious code. From then on, the script was automatically sending the private keys of MyDashWallet users to an external server presumably under control of the attackers. “This change was detected on July 12 2019 when the hacker used the private keys to move user funds,” clarified Leon White, who manages Dash’s documentation and Wiki.
The full amount of lost DASH is still unknown
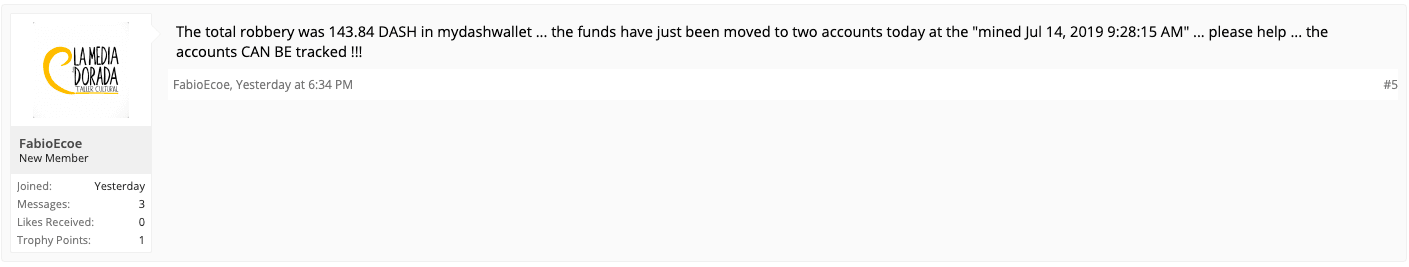
As yet, the total amount of cryptocurrency stolen from MyDashWallet users over the past two months isn’t clear. Sadly, one MyDashWallet user has already claimed to have lost 143.84 DASH ($17,597) to the hackers. According to MyDashWallet, those who used its service in conjunction with hardware wallets or “associated tipbots” are apparently not affected. The firm also doesn’t believe the vulnerability extends to other third-party wallets. In order to avoid situations like this in the future, White warned that all code that handles DASH private keys should be “reviewed thoroughly” before it is trusted to handle user funds.
White also urged services to discourage the use of local keystores in favor of hardware wallets. “The hack itself was only active for two months before being detected. The insecure coding practice implemented by MyDashWallet went undetected for over a year due to insufficient review of code by third parties,” said White. “MyDashWallet is not maintained by Dash Core Group, and at no time was the Dash network itself compromised.” Hard Fork has reached out to MyDashWallet to learn more about the full extent of the attack, and will update this piece should we receive a reply. Update 17:05 UTC, July 16: A MyDashWallet spokesperson has since contact Hard Fork to provide more insight. They explained that the malicious code was built to read the keystore files and private keys of users, later sending them to a domain that has since been deleted. The representative told Hard Fork that only users who had used a browser without any cached data for the MyDashWallet website had been at risk, as they would have needed to download the compromised script to be affected by the attack. Older users and MyDashWallet admins reportedly weren’t affected, as their browsers would have saved a safe version of the script to their caches. The spokesperson noted this to be the reason for the vulnerability’s untimely discovery. “We only have heard from a few users contacting us or Dash Core about this issue, we don’t know how many users are really affected,” the spokesperson told Hard Fork in an email. “Most users use hardware wallets or other services (mixing, tipping, bots, etc.) on the website and are not affected at all, we still recommend users that created a HD Wallet in late May or June to create a new wallet and move all funds over there,” they added.